RiskIQ, the global leader in digital threat management, recently released an infographic mapping and profiling the global cryptocurrency mining landscape, which has swelled in size due to the rush by companies and threat actors alike to capitalise on cryptocurrency's skyrocketing valuation.
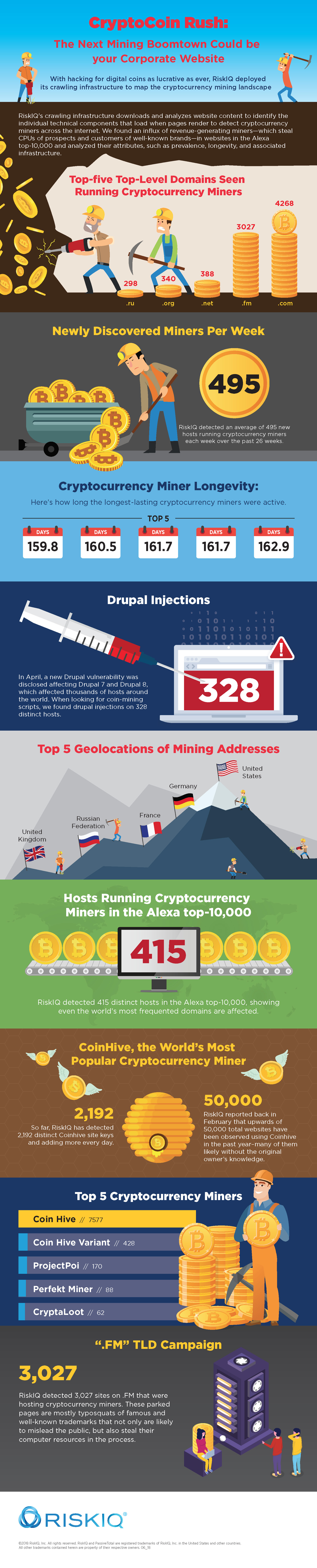
The infographic is based on data collected by RiskIQ's web crawling infrastructure, which downloads and analyses website content to identify the individual technical components that load when rendered to detect cryptocurrency miners across the Internet. The research highlights the influx of revenue-generating miners in domains in the Alexa top-10,000 and analyses their attributes, such as prevalence, longevity and associated infrastructure.
Since these miners require an expensive amount of computing power — Fundstrat reported that the cost of mining a single Bitcoin reached about $8,038 and the costs of mining other coins are not far behind — actors often source it from unwitting users. To do so, they take advantage of the fact that security teams lack visibility into all the ways that they can be attacked externally and struggle to understand what belongs to their organisation, how it’s connected to the rest of their asset inventory and what potential vulnerabilities are exposed to compromise.
While some brands capitalise by running cryptocurrency mining scripts in the background of their sites to leverage the computers of their visitors legally, threat actors exploit this blind spot to hack vulnerable sites or spin up fake, illegitimate websites to siphon money, often with typosquatting domains and fraudulent branding. RiskIQ reported back in February that an upwards of 50,000 total websites have been observed using Coinhive in the past year–many of them likely without the original owner’s knowledge.
"In the case of cryptocurrency mining scripts, organisations must be able to inventory all the third-party code running on their web assets and be able to detect instances of threat actors leveraging their brand on illegitimate sites around the Internet,” said Adam Hunt, chief data scientist at RiskIQ. “Threat actors realise the lack of visibility these organisations have and are targeting it accordingly.”
The report found that threat actors leveraging domains or subdomains that belong, or appear to belong, to major brands, trick people into visiting their sites running cryptocurrency mining scripts to monetize their content.
(Source: RiskIQ)